PII Data Vault
Secured processing of sensitive customer data using cryptographic computing & searchable encryption

Next Frontier in Data Protection starts with PII Data Vault
In today’s AI-driven world, where data fuels every decision, protecting personally identifiable information (PII) is no longer optional.
It’s imperative!
With rising concerns on protection against cyber attacks and data breaches,privacy concerns, evolving global regulations, and increasing scrutiny on cross-border data flows, organizations need more than just traditional encryption. They need a smarter, secure-processing approach to protect PII without compromising usability.
They need a PII Data Vault.

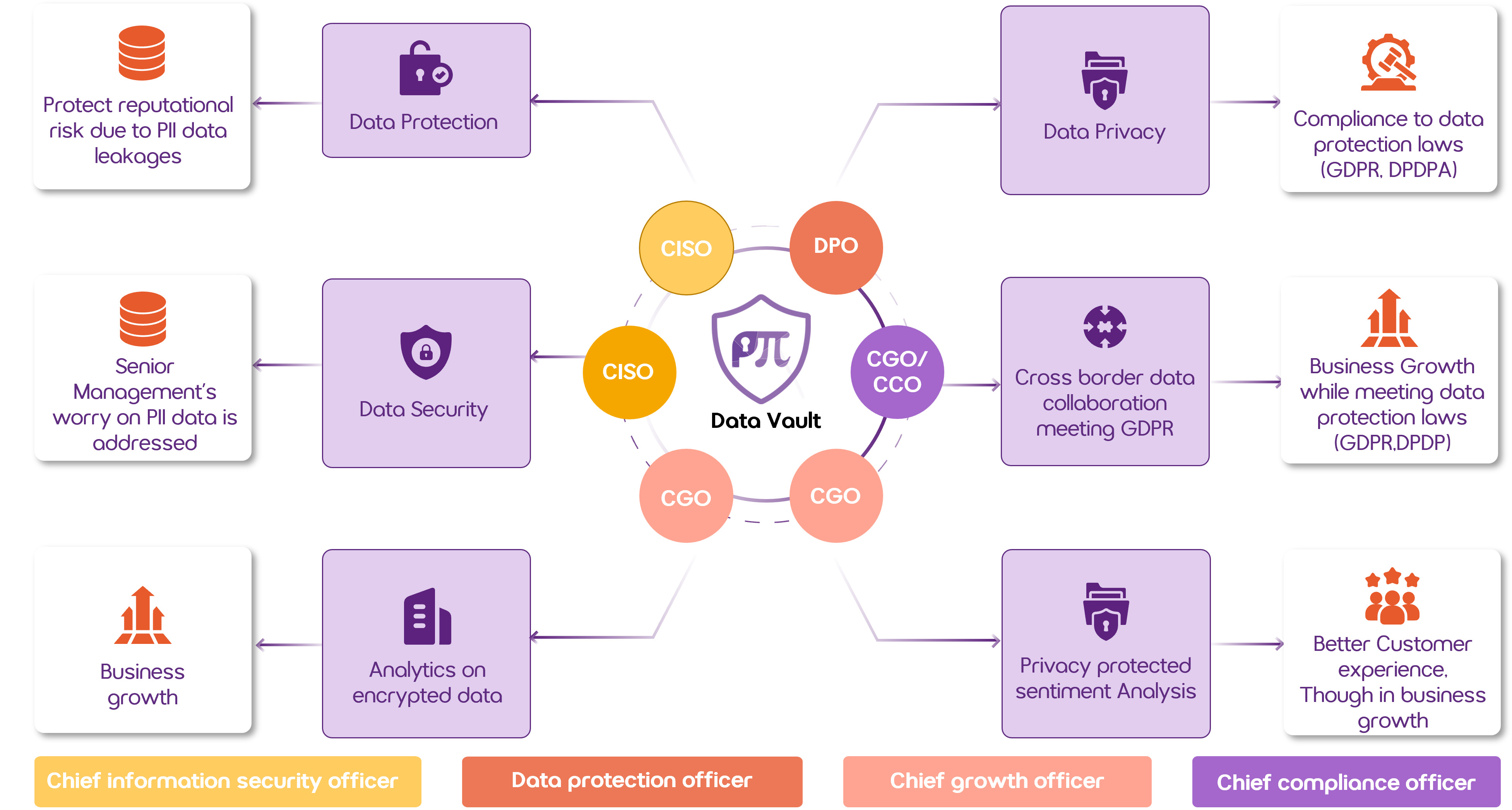
Adopt the Proactive Way of Data Protection

Why PII Data Protection is a Must Have Reputation & Revenue Risk
Privacy and security breaches cost high
$4.88M - Average cost per data breach globally
- IBM’s Cost of a Data Breach Report 2024.
Huge Regulatory fines for data breaches:
under GDPR, DPDPA

Strengthen PII Data Protection From Cyber Attacks & Breaches with Zero Data Exposure
Traditional encryption methods like AES-256 or AES-512 protect data but limit usability.
To search or analyze encrypted data, it must first be decrypted, exposing sensitive information in the process.
Posidex’s PII Data Vault changes the game.


Built on searchable encryption and zero data exposure, it allows you to search, match, and process encrypted PII without ever decrypting it. Unlike conventional vaults that simply store keys, our vault processes encrypted data directly, enabling privacy-first intelligence at scale.
This is next-generation data security, purpose-built for an AI-driven, regulation-heavy world.
Unlock tangible business value across data functions
Protection & Usability. Simultaneously. Without decrypting PII data.
Proprietary hashcryption algorithm
The basic version performs exact search of data elements.
The advanced version performs exact and fuzzy search on name and date elements
Enriched Fully Homomorphic Encryption algorithm
Certified FHE algorithms plus proprietary algorithm process all data elements (strings, dates, numbers) in encrypted form
Format Preserving Encryption
Based on NIST-approved algorithms for secure data use in legacy systems without changing schema or validation logic
Sentiment analysis on PII
Privacy preserving data discovery, data transformation and sentiment analysis on anonymized PII data using LLMs
It solves the biggest sensitive PII data challenges
Privacy Preserved Processing
Uses proprietary probabilistic, randomized hashcryption, and enriched fully homomorphic encryption algorithms to keep data secure even during processing.
Localization Laws
Customer PII stays within national boundaries with limited access to plain text data across borders, supporting localization laws
Fuzzy Search
It performs a probabilistic search on all data, keeping you fast without breaking privacy
Data Security
Queries are encrypted and compared without exposing plain text data
Resource Saving
Limited additional overhead in terms of response time, compute or storage
Data Protection
Data is always encrypted so even internal or external hackers cannot see it
Application in every industry dealing with customer data


















.svg)

